Why CrowdStrike is Essential for Security
Cyberthreats to your business are at an all-time high. They are, as President Biden states, “the defining threats of our time.” Is your company prepared to withstand such attacks? According to a recent Gartner article, business leaders need to do more to strengthen their cybersecurity.
![]()
“There are only two types of companies: Those that have been hacked and those that will be hacked.”
Robert S. Mueller, former Director of the FBI – 2012
![]()
“There are only two types of companies: Those that have been hacked and those who don’t know they have been hacked.”
accredited to John Chambers, CEO Cisco – 2019
Days before Russian tanks began rolling into Ukraine; a significant connectivity outage hit Viasat Inc. (VSAT). The Carlsbad, Calif.-based company is a leading provider of high-speed satellite broadband and secure networking for military and commercial customers worldwide. Viasat modems control thousands of wind European wind turbines. Suddenly, they went offline. The outage hobbled the Ukrainian military as generals began preparing for the Russian invasion. Reuters later reported the blackout to be sabotage.
Although most well-organized ransomware gangs are in Eastern European countries, state-sponsored hacking groups are from China and North Korea. They use sophisticated tools to embed malware deep inside the most extensive networks. In many cases, malicious code can go undetected for months, infecting millions of computers.
On January 15, 2022, members of one of the main ransomware gangs, Our Evil Group, were arrested in Russia. The Putin regime has recruited them to become a state-controlled group of hackers. About a month later, we began to see a resurgence of attacks. And that’s only the attacks we read about in the headlines. For every ransomware attack you hear about, there are three others that go unreported.

Hackers used a software supply chain attack to insert malicious code into the company’s Orion system. A supply chain attack works by targeting a third party with access to an organization’s systems rather than hacking the networks directly.
The Software Supply Chain Attack
SolarWinds is a company that supplies its software to over 14,000 companies. Russian military intelligence inserted a form of malware that served as a sophisticated backdoor to these companies. It’s a certainty that some of these backdoors have been successfully embedded without US companies knowing about it. Corporations probably can’t determine conclusively whether-or-not a backdoor has been installed.
In the case of the SolarWinds Corporation, one of their customers, a cybersecurity company called Fire Eye, discovered the malware by chance. They had received the software and, months later, somebody noticed a questionable anomaly. SolarWinds is not a unique situation. There are sure to be other corporations that have been infiltrated.
Escalation of Ransomware Attacks
Recently, the President sent warnings to the citizens and businesses across the country and urged everyone to take steps immediately. Key targets include private companies and any organizations that could apply pressure to the national economy and the government, including critical infrastructures.
When it comes to ransomware attacks, no sectors are off-limits. Hackers are going to go after everything that they can. Last year, we saw how no company, large or small, was immune to attack. For example, there were ransomware attacks on the following:
- Small Family-Run Fishing Business
- Ferry company on Martha’s Vineyard
- Casino Hacked through a Fish-Tank Thermometer
- Large meatpacking company
- The Colonial Pipeline

Raleigh, NC United States- 05-12-2021: A red plastic bag covers an empty pump at a gas station in Raleigh, NC, after a devastating cyberattack on the Colonial Pipeline disrupts fuel supplies on the East Coast.

Nicole Perlroth assembles her decade of experience as the world’s leading journalist on cybersecurity and digital espionage in an in-depth history of cyberwarfare entitled THIS IS HOW THEY TELL ME THE WORLD ENDS. In it, she warns of the rising stakes for all of us.
The Colonial pipeline was devastated in May 2021 by cyber terrorists. Attackers distributed malware through email then demanded a ransom to restore services. The 5,500-mile pipeline transports 100 million barrels of gasoline and other fuel products per day to the eastern United States. According to a report from Reuters, gasoline futures spiked 3% and have remained above trend since that time.
Two months later, Jennifer Granholm, the Energy Secretary, said that bad actors gained the ability to shut down the U.S. power grid. Hackers embedding themselves in the nation’s electrical grid displayed tremendous sophistication that analysts hadn’t seen before. Whoever was behind the cyber-attacks on our country’s infrastructure was succeeding at an alarming rate. Who did the government call in to investigate? CrowdStrike. Why? Because CrowdStrike has been investigating high-profile cyberattacks since 2011. Investigators at CrowdStrike have even unspooled more recent attacks where the code dates back to 2010. So, CrowdStrike has been on the frontlines of cybersecurity since their beginnings.
What Can Be Done?
There are basic preventative steps that everyone must apply regularly. For example, don’t respond to SMS text messages from unknown origins. Don’t open links from emails of anonymous sources. Make that a personal policy and individuals will effectively eliminate most threats. Companies, on the other hand, are different. They need comprehensive and robust security protocols that are more sophisticated than the attacks.
Companies must realize that antiquated technologies like antivirus and firewalls are weak defenses against modern, sophisticated cyberattacks. Businesses must modernize their cybersecurity by using the new technologies mentioned by President Biden in his message to the nation. Businesses must use security measures like EDR and XDR to protect against modern ransomware groups.
EDR stands for Endpoint Detection and Response. It’s an integrated endpoint security measure that combines real-time continuous monitoring and collection of endpoint data with rules-based automated response and analysis capabilities. In the case of CrowdStrike’s EDR, the security technology combines a high degree of automation with machine learning to enable security teams to identify and respond to threats immediately. The next-generation endpoint protection leverages CrowdStrike’s state-of-the-art file and behavioral-based proprietary machine learning and Indicator-of-attack methodology. This is particularly effective at stopping new, polymorphic or obfuscated malware, which is often missed by legacy antivirus solutions.
An essential ingredient of “next-generation” is reducing overhead, friction, and cost in protecting your environment.
You don’t need a large staff to maintain the CrowdStrike environment. Everything is cloud-based, so there’s no equipment to maintain, manage or update. The Falcon sensor is unobtrusive, and updates are seamless, requiring no re-boots. The web-based management console provides an intuitive and informative view of your company’s complete environment.
XDR is Extended Detection and Response and is the evolution of having EDR as a pre-requisite technology. CrowdStrike’s Falcon XDR uses artificial intelligence to improve threat visibility by making sense of structured and unstructured data at lightning speeds. Falcon XDR rapidly and efficiently hunts and eliminates threats across multiple security domains. What separates Falcon XDR from all others is its ability to isolate and identify relevant telemetry from systems and applications across an organization’s entire IT security ecosystem. Falcon XDR delivers proactive, automated responses to threats across the security stack.
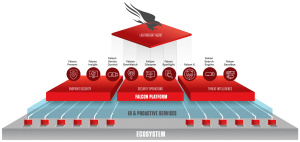
CrowdStrike® Falcon® Complete™ is a hands-off and worry-free managed detection and response (MDR) solution. The comprehensive security platform is unique. In addition to endpoint security, cloud workload, and identity protection, it provides the process and technology required to handle all aspects of onboarding and configuration to maintenance, monitoring, incident handling, and remediation.
CrowdStrike’s Falcon Complete protects an organization against someone clicking on a link they shouldn’t have. The technology sees the behavior, and as executable files begin unzipping, Falcon Complete begins monitoring for questionable activity. As soon as malicious activity, Falcon Complete isolates it.
Why CrowdStrike?
CrowdStrike has been leading the charge against cyberthreats since 2011 when it was founded. The security firm uses cloud-based software that collects threat data across all connected devices. Artificial intelligence analyzes the information and seamlessly updates all endpoints.
The fast-growing Austin, Texas-based company provides cybersecurity to 15 of the 20 largest banks and 77 Fortune 100 companies. Private sector clients are apprehensive about the escalation of cyberthreats against Americans amid Putin’s invasion of Ukraine. Severe ransomware attacks are likely to increase as sanctions on Russia become more effective.
CrowdStrike has a long history of working with the federal government state, and national oil and energy firms to investigate cyberattacks and shore up defenses. Much of their innovations in security came from listening and working with clients to help solve the most challenging cybersecurity problems. Years of forensic analysis, fine-tuning, and adjusting to meet threats as they emerge have made CrowdStrike the pioneer of cloud-delivered endpoint protection.
CrowdStrike Falcon has revolutionized endpoint security by being the first and only solution to unify next-generation antivirus, endpoint detection and response (EDR), and a 24/7 threat hunting service. Millions of sensors across 176 countries collect and analyze more than 30 billion endpoint events per day. All of them use some form of machine learning and automation. These powerful capabilities are possible through a unique combination of prevention technologies. They include indicators of Attack (IOA), exploit blocking, real-time visibility, and around-the-clock managed hunting to discover and track the stealthiest attackers before they do damage.
The country cannot defend against cyberattacks alone, nor can your organization. Companies need the vigilance of every employee and every contractor. Business leaders must “accelerate efforts to lock their digital doors.” Using CrowdStrike is an effective way to secure all entries to your company’s infrastructure.
IronOrbit knows the importance of having resilient cybersecurity. That is why we protect our virtual desktops, INFINITY Workspaces, with CrowdStrike’s highest level of AI-enabled security technology augmented by live monitoring by a team of CrowdStrike’s team of security experts. Imagine having multiple full-time expert incident responders conducting day-to-day monitoring of alerts.
CrowdStrike® Falcon® Complete™ is a 100 percent hands-off and worry-free managed detection and response (MDR) solution uniquely provides the people, process, and technology required to handle all aspects of endpoint, cloud workload, and identity security, from onboarding and configuration to maintenance.
Learn more about how to protect your company here.
or Call us at (888) 753-5060.